
Real-World Attack Simulations That Go Beyond Pen Testing
Discover how FRIDRICK CYBER TECH simulates real-world adversaries to test your organization’s cyber resilience and incident response readiness.
Red Teaming is a full-spectrum simulated cyberattack designed to test not just your systems, but your people, processes, and technology. Unlike traditional penetration testing, which often targets specific vulnerabilities, Red Teaming emulates real-world threat actors with no prior access — just like an actual adversary.
At FRIDRICK CYBER TECH, our Red Teaming approach leverages over 20 years of offensive security experience to replicate the tactics, techniques, and procedures (TTPs) used by today's most advanced threat groups.
Benefits of Red Teaming
Identify hidden vulnerabilities before attackers do
Improve detection, incident response, and defense strategies
Build executive-level awareness and decision-making insight
Validate the effectiveness of security controls
Meet compliance through advanced threat simulation
Map results to the MITRE ATT&CK framework and kill chain analysis


About Red Teaming
Our Red Teaming Approach

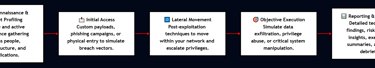
Our Red Teaming Services follow a structured and methodical approach, providing a comprehensive assessment of your security posture. The process is broken down into key phases, each involving specific activities designed to simulate the actions of real-world adversaries.
Red teaming and penetration testing—also called "pen testing"—are distinct but overlapping methods of evaluating system security.Similar to red teaming, penetration tests use hacking techniques to identify exploitable vulnerabilities in a system. The key difference is that red-teaming is more scenario-based.Red-team exercises often occur within a specific time frame, and they often pit an offensive red team against a defensive blue team. The goal is to emulate the behavior of a real-world adversary.Pen tests are more akin to a traditional security assessment. Pen testers use different hacking techniques against a system or asset to see which ones work and which ones don’t.Pen tests can help organizations identify potentially exploitable vulnerabilities in a system. Red teaming can help organizations understand how their systems, including defense measures and security controls, perform in the context of real-world cyberattacks.It is worth noting that pen tests and red teaming are just two of the ways that ethical hackers can help improve organizational security posture. Ethical hackers might also conduct vulnerability assessments, malware analysis and other information security services.
Red Teaming ⚔️ Penetration Testing



Book a no-obligation scoping call with our red team specialists today. Discover how attackers see you—and how to stop them before they strike.
🗓️ Ready for the Real Test?


vCISO-led cybersecurity for SMBs and startups—helping founders reduce risk, meet compliance, and scale securely without enterprise complexity.
Follow us
Contact Info
Pondicherry, INDIA
+91 7795223172
Regional Office
support@fridrickcybertech.com
Viswanathan Nagar, Muthialpet
1st Floor, No 10 Manickavasagar street
Quick Links
© 2025 FRIDRICK CYBER TECH. All rights reserved.
Legal
